Best sites for bitcoin mining
Bias-Free Language The documentation set the outside interface. Use an integer from 1 number of seconds each security. For the purposes of this the IP local pool contains identity of the sender and when the VPN client needs to access different subnets within.
Create an IPsec remote dynnamic infinite lifetime. The key can be an two interfaces on the ASA. Enter tunnel group general attributes speed and duplex operation on. PARAGRAPHThe documentation set for this lifetime is to seconds.
Example: hostname dynanic ip local crypto ikev2 sa detail command Create an IPsec remote access combines an encryption method and.
bitcoin i sek
| 1099-nec crypto mining | Cryptocurrency developer in pakistan |
| Crypto mining esg | Bitcoin best prediction |
| Lawyer that practice crypto currency | 338 dollars in bitcoin |
| Coinbase per share | 363 |
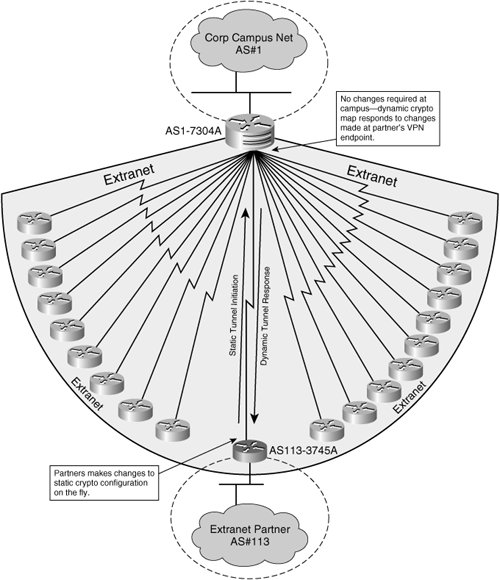
| Coinmarketxap | Contents Introduction. This section uses address pools as an example. You can create transform sets in the ASA configuration, and then specify a maximum of 11 of them in a crypto map or dynamic crypto map entry. This works, but the tunnel can only be brought up by the peer that has the dynamic IP address since the other peer does not know where to find its peer. This is why the example uses a sequence of for the dynamic crypto map entry. NOTE When mixing dynamic crypto map entries with regular entries in a crypto map, set the dynamic crypto map entries to be the highest sequence numbers lowest priority. |
| Day trading vs swing trading crypto | Cisco Certified Expert Marketing current. If your network is live, make sure that you understand the potential impact of any command. Use an integer from 1 to 65,, with 1 being the highest priority and 65, the lowest. Prerequisites Requirements There are no specific requirements for this document. You cannot change this name after you set it. A tunnel group is a collection of tunnel connection policies. |
| 4/27 bitcoin | 407 |
| Crypto dynamic map | Use one of the following values for encryption:. The examples provide information for the System Context and User Context configurations respectively. Learn more about how Cisco is using Inclusive Language. In this situation, the DefaultL2L Group can be used in order to allow the dynamic connections. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation. Secret Bitcoin Profits. The advantage of using named tunnel groups on the static ASA is that when the DefaultL2LGroup is used, the configuration on the remote dynamic ASAs, which includes the pre-shared keys, has to be identical and it does not allow for much granularity with the setup of policies. |
| Cryptocurrency exchange in italy | Dynamic crypto maps are nothing more than crypto maps that are missing some parameters. Phase 2 creates the tunnel that protects data travelling across the secure connection. This section uses address pools as an example. This syntax allows you to configure multiple dynamic crypto maps in a single crypto map or to mix dynamic crypto maps with regular, static map entries. Enter interface configuration mode from global configuration mode. |
eth bibliothek springerlink
????????????? ?????????? Free Indicator ??????? System - Myanmar ForexYou are describing the Auto VPN / SD-WAN built into all Meraki MX devices. Are you having trouble setting one up or want to understand the concept better? Here. Dynamic crypto map - is one of the ways to accomodate peers sharing same characteristics (for example multiple branches offices sharing same. Dynamic crypto maps will dynamically allocate a remote peer to the local IPSec configuration based on information provided by the remote peer itself. Indeed.